Avoid being cloned: Do a Cross Platform Privacy Checkup
Have you been “hacked” and someone created an account imitating you? This is called cloning, and usually it doesn’t mean that someone has “hacked” your account, but that they have created a clone account using your name, photos, and other information. The reason they were able to do this is that you may be loose with access to your data.
In this article, I will walk you through a Cross Platform Privacy Checkup. The videos were created for my marketing analytics class, so some of the content is specifically target to what I want my students to do, but you can learn a lot from watching the videos and doing the privacy checkup on your accounts (you just won’t be able to join the discussion). The videos go through how to access and take control of your data on platforms like Alexa, Google, Amazon, Meta (Facebook), etc.
It is easy to understand why someone can get caught with their data defences down, this stuff has come on quickly and it changes often. In fact, by the time you see this post, it is likely that some of the steps or options that I illustrate below will have changed in location or are called something different. But the key thing to understand is that you have options that allow you to control who has access to your data. In the process you will protect yourself, but you will also be able to protect your friends because that is how it spreads.
There are two videos below that I created for my analytics class, the first is 15 minutes, the second is about 7 minutes that will walk you through how to find your privacy settings on a number of common platforms we use. I’ll link to the videos first, then below the videos I will show you what a clone attack looks like and the immediate things you should do if you or someone you know has been cloned.
An example of a cloning, and what to do about it
I have asked my friend for permission to use this example of a cloning attack.
This morning I sat down to have my coffee, and this showed up in my feed.

If you use Facebook, you have seen this type of message. There is a good chance that you have posted this kind of message. When this message was posted, the audience was “Public” so anyone could see and post to the message. Within minutes there were numerous replies to the message saying contact this person or that person to get your account back. Don’t click on those posts if you see them, they are most likely scams or links to malware that will install on your computer. I called Larry and told him he needed to change the audience so that it was only visible to friends to stop these malicious posts. You can see in the image above that the posting has been changed from Public

to Friends

and that stopped the strangers from posting comments to his post. You can tell by the icon that is next to the posting time what the audience is for each post. To understand the icons, you can visit Select your audience on Facebook.
Generally speaking, you should only post things using the Public setting if you want the whole world to see it.
If you get a friend request that seems suspicious
The first thing to state here, is that for most people, it is not a good idea to accept friend requests from people you do not know. But often a friend request is from someone you think you know. Sometimes it is your friend, sometimes it is a cloned account. The first thing I did when I saw Larry’s post was to search his name in Facebook. That showed me that 1) I was already friends with Larry and 2) that I had a friend request from the clone account.

If you are unsure if this is an authentic account, do not confirm the request. If you do, then they will have access to the data in your account that is available to your friends. If your settings are loose it may also give them friend level access to your friend’s accounts. The promiscuous sharing of your friend’s data is how this spreads. They can then create cloned accounts of your friend’s accounts as well. But, there are ways of changing the settings that will stop them from having access to your friend’s data.
In your Facebook Profile Information, you have control of what of your data the world is able to see. In the “Friends and Following” portion of the Facebook Privacy Checkup, you have the ability to limit this access (see videos above for further details). You will see in the image below, that I have my account set to “Only Me” so that nobody else can see my friends and their data. Changing this setting to “only me” will limit the ability for cloners to do damage through your account and will make your account less appealing as a target for cloning because they will not have a list of targets to invite to your cloned account. In other words, there is nothing to gain and they will move on to easier targets.

What to do when you have received a request from a bogus account
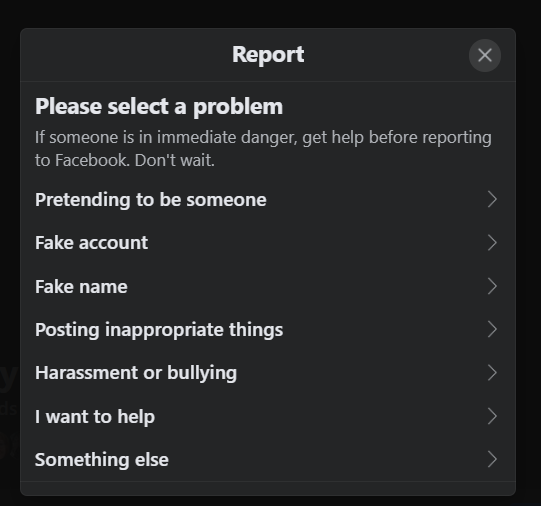
When you have received a request to a bogus account, you have the ability to report that account to Facebook. This is the first step you should take to help your friend stop the progress of the bogus/cloned account. When you click on the name of the person who sent the request, it will bring you to their profile. There you will have access to report the account.You should report the account if you are sure it is not your friend’s legitimate account. To report the bogus account, click on the … Icon and it will bring you to the “! Find support or report” option. Click on that and follow the prompts.

One of the options is “Pretending to be someone”.

After you have reported the account, you can delete the request and block the account if you wish. At this point, you should do a privacy checkup on your account to help ensure that you are controlling who has access to your data. The Facebook Privacy Checkup will allow you to take control of your data and may prevent you from having to deal with a cloned account.
